14 AWS Cloud Security Best Practices You Must Know About: Part 1

Did you know nearly half of all security breaches happen in the cloud? 80% of companies dealt with a cloud security issue over the last year. What’s even more eye-opening is that more than 60% of those incidents were tied directly to using public cloud services like AWS in 2024. These figures make it clear: cloud security is now more important than ever.
As companies lean more on Amazon Web Services (AWS) for their cloud setup, they encounter various security hurdles. Issues like misconfigured S3 buckets that risk exposing private data and weak identity and access management can open systems to attack. With cyber threats continuously changing, keeping your AWS environment secure is a challenging task. However, don’t worry—there are effective ways to strengthen your AWS security. In this first part, we're laying down the basics before we go into AWS security best practices. We're going to break down what AWS Cloud Security is all about, get a grip on the core ideas behind it, and highlight those important AWS components that really need our focus when it comes to keeping them safe—both now and in the long run.
What is AWS Cloud Security?

AWS Security refers to the combination of tools, practices, and services used to protect data, applications, and systems hosted on Amazon Web Services. It's essential for organizations that depend on AWS to store and access their digital assets while ensuring secure operations. These standard protocols are built-in to keep your cloud infrastructure as secure as possible. It’s a shared responsibility: AWS secures the cloud, while customers secure their operations within it.
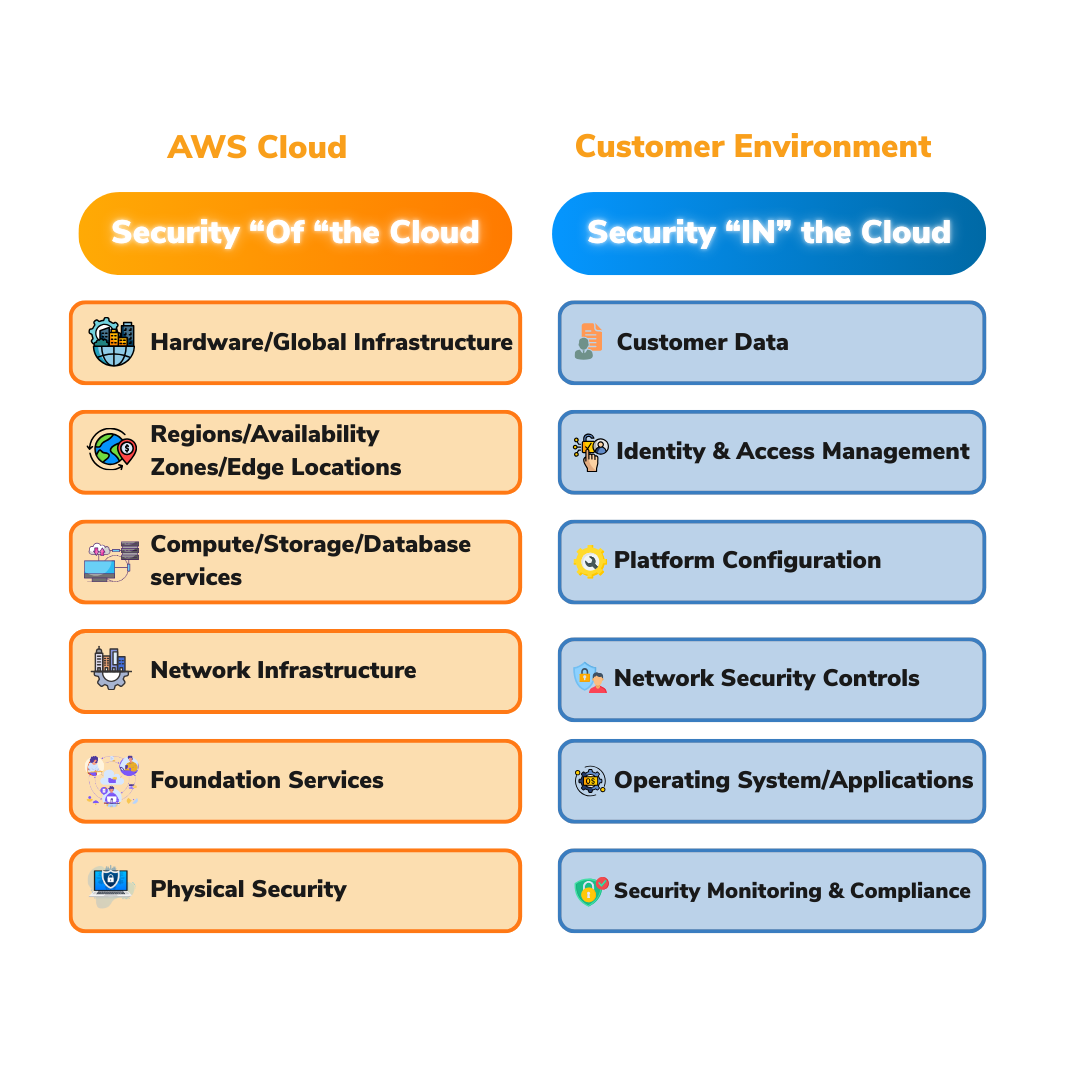
(Image: AWS Shared Responsibility Model)
Is AWS Cloud Security Different from Traditional Security?
So, how does this differ from traditional security? Well, traditional security focuses on protecting a fixed infrastructure. The security measures for these static setups are designed for relatively stable and predictable environments.
In contrast, with the right cloud security setup, resources can be quickly adjusted, which means security must adapt in real-time. AWS offers tools like Identity and AWS IAM (Access Management), AWS encryption, and network firewalls to help users maintain strong defenses while taking full advantage of the cloud's flexible scalability.
Key Aspects of AWS Security

Here’s a quick look at the key aspects of AWS security that help protect your cloud infrastructure and resources:
- Data Encryption
Safeguard sensitive information with encryption protocols for both stored and transmitted data.
- Access Control
Set up detailed access controls with Identity and Access Management (IAM) to ensure users have only the permissions they need.
- Infrastructure Monitoring
Use tools like AWS CloudTrail and Amazon GuardDuty to monitor activities in your infrastructure constantly.
- Threat Detection and Mitigation
AWS Security Hub helps you detect, analyze, and tackle potential threats throughout your AWS environment.
- Compliance Automation
Easily automate AWS compliance checks with AWS Config to meet regulatory standards without hassle, including areas like AWS HIPAA compliance.
- Least Privilege Enforcement
Limit access strictly to what’s necessary, reducing the chance of unauthorized use or exposure.
Which AWS Components Need Security Attention?

Securing your AWS environment is a collaborative effort, and a few crucial components are the backbone of your security. First off, understanding the Shared Responsibility Model is essential: AWS takes care of the underlying cloud infrastructure, while you, as a customer, need to secure what you build on AWS—your applications, data, and user access.
To effectively protect your setups, here are the key AWS components that need your attention:
- Identity and Access Management (IAM): It's vital to manage user permissions and roles (AWS IAM role) to control access to your AWS resources.
- Network Configuration (Amazon VPC, Security Groups, NACLs, AWS Network Firewall, AWS Shield): Configuring your virtual network properly with Security Groups, Network ACLs, and protections like AWS Network Firewall and AWS Shield is essential to fend off threats.
- Data Storage (Amazon S3, Amazon EBS, Amazon RDS): (Amazon S3, Amazon EBS, Amazon RDS): Use built-in AWS encryption for EBS and S3, along with AWS Key Management Service (KMS), to ensure your data is secure.
- Compute Resources (Amazon EC2, AWS Lambda, Amazon ECS/EKS): Keep your virtual servers and serverless functions secure by patching, hardening, and managing access.
- APIs and Application Integration (Amazon API Gateway): Protect your APIs to prevent unauthorized access and data leaks.
- Monitoring and Logging (AWS CloudTrail, Amazon CloudWatch Logs, Amazon GuardDuty): Stay ahead of potential threats with logging, monitoring, and detection services for effective incident response.
By focusing on these core AWS components and utilizing AWS's security features, you can create a robust security stance in the cloud, aligning with the principles of the AWS well architected framework.
Alright, so keep an eye out for Part 2, where we'll be looking at the typical hurdles that companies run into while setting up AWS security. Plus, we’ll dig into a solid list of smart strategies to strengthen your cloud setup, potentially even touching upon an AWS security best practices checklist. Sounds good?
Ready to Strengthen Your AWS Security?
Don’t leave your cloud assets vulnerable. Contact our AWS experts today for personalized advice and insights tailored to your unique needs. Get in touch now to learn more about how we can help you implement the best practices in AWS security and ensure your operations are secure and compliant!
At the Heart of SJ Innovation: How we Coordinate our International venture

FRIDAY FUN ACTIVITY : A MUST AT EVERY WORKPLACE


