Learn AWS VPC in just a few minutes!

Do you remember when we used to spend a great deal of our time purchasing devices? Conducting setup and configuration of the networks in our onsite data centers? However now, things are different owing to the power of AWS!
AWS cloud services have made it very easy that we can perform this entire setup within a few clicks. This blog is an AWS VPC tutorial that talks about one of the services offered by AWS to configure networking within AWS — Virtual Private Cloud (VPC).
What is AWS Virtual Private Cloud (VPC)?
If you are wondering what is AWS Virtual Private Cloud all about, Amazon VPC enables the launch of AWS resources into a virtual network that you have defined. The AWS VPC network is a virtual network. It closely resembles a traditional network that you would operate in your own data center, with the benefits of using the scalable infrastructure of AWS. We can have multiple VPCs in a region (max 5 per region) and the max CIDR per VPC is 5. VPC is a private network where only a private IP range is permitted. It’s crucial to ensure that CIDR does not overlap with other networks.
If you wonder if AWS VPC is free, it’s important to know that there are no additional charges for creating and utilizing the VPC itself. However, usage charges for other Amazon Web Services including Amazon EC2 are still applicable at published rates which also include data transfer charges.
What is Default VPC in AWS?
If you go through any AWS VPC tutorial, you may come across default VPC in AWS. Default VPC is the pre-configured network in AWS. All new accounts will have default VPC. New instances are launched into default VPC if no subnet is specified, default VPC has internet connectivity and all instances have a public IPv4 address. If there was no default VPC then it would have become very difficult for newcomers to configure it.
What are the important components of VPC?
Before you setup AWS VPC, you need to know about a few of its vital components.
Subnet: What is AWS VPC subnet? A subnet refers to a range of IP addresses in the VPC. The subnet mask defines how many bits can change in an IP address. AWS reserves 5 IP addresses (first 4 and last 1) in each subnet.
Internet Gateway: An internet gateway helps VPC instances to connect with the internet. One VPC can only be attached to one IGW and vice versa.
Router: Routers interconnect subnets and direct traffic between the internet gateway, virtual private gateways, NAT gateways, and subnets.
Peering connection: The peering connection is used to connect two different VPCs. It is a networking connection between two VPCs for routing traffic between them with the help of IPv4 addresses or IPv6 addresses.
VPC Endpoint: VPC endpoints are horizontally scaled and enable the creation of a private connection between VPC to supported AWS networks. It is a private connection to public AWS services.
NAT Gateway: NAT gateway is a Network Address Translation (NAT) service that enables internet access to instances in private subnets and is managed by AWS. You can utilize a NAT gateway to ensure instances in a private subnet can connect to services outside your VPC. However, external services cannot initiate a connection with those instances.
Security Group: Security group is instance level firewall that keeps a watch on incoming and outgoing traffic. Inbound rules manage the incoming traffic to your instance and outbound rules look after the outgoing traffic from your instance. When launching an instance, you can specify one or more security groups.
Network ACL: A Network ACL (Access Contol List) is a layer of security for your AWS VPC network. It is a subnet-level firewall and permits or denies specific inbound or outbound traffic at the subnet level.
Private and Public IP addresses range that help create subnets
Private IP addresses can be used within a network without internet access. Ranges can be:
10.0.0.0/8 – Used for big network
172.16.0.0/12 – Default AWS range
192.168.0.0/16 – Used in small networks
All of the other IP addresses on the internet are public IP addresses.
Practical implementation of VPC in AWS
We will create one Default VPC, 2 private subnets, 2 public subnets, launch ec2 instance using public subnet, internet gateway and route table. We should be able to ssh into ec2 instance.
Go to the AWS console and select VPC and click on Create VPC, already there will be a default VPC.
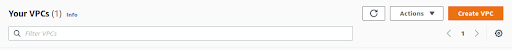
On the Create VPC window give the VPC name as Demo VPC and add IPv4 CIDR.
Put CIDR block range as 10.0.0.0/16 which will give 65536 ip address.
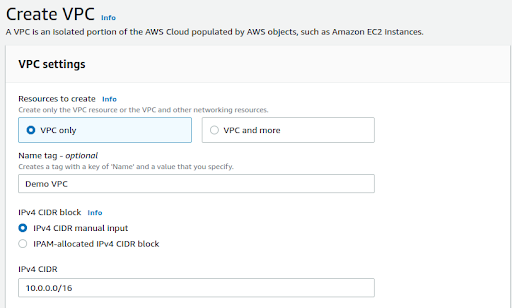
Next, we need to create Subnets. Click on Subnet and then click on Create Subnet. Default subnets will be present under subnets.

In the Create Subnet window select VPC id as Demo VPC which we have created and add Subnet name, select availability zone and add IPv4 CIDR block. We will create 4 subnets 2 Public and 2 Private.
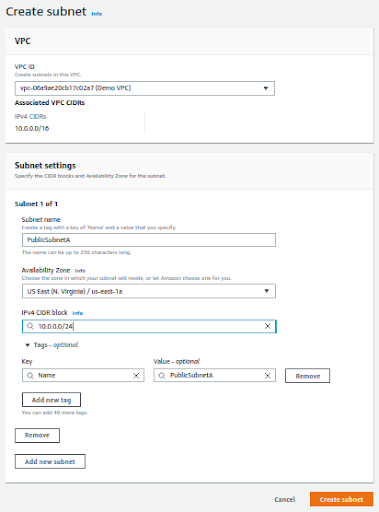
Click on Add new subnet and add remaining below mentioned public and private subnets
PublicSubnetA – 10.0.0.0/24 which will give 256 ips and select AZ us east 1a
PublicSubnetB – 10.0.1.0/24 which will give 256 ips and select us east 1b
PrivateSubnetA – 10.0.2.0/24 which will give 256 ips and select us east 1a
PrivateSubnetB – 10.0.3.0/24 which will give 256 ips and select us east 1b
Next launch an ec2 instance and select the Public subnet which is created under Demo VPC and also enable Auto-assign public IP. Try to SSH into an instance but it will not work. Let's see what is wrong in the next step.
Next we need to Create an Internet Gateway and attach it to the Demo VPC which we have created.
Go to Internet gateways and click on Create internet gateway
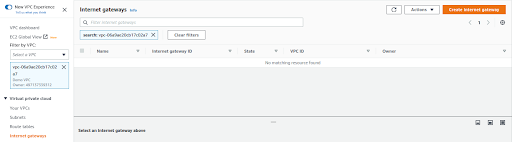
Under Create internet gateway window give Name tag as DemoIGW
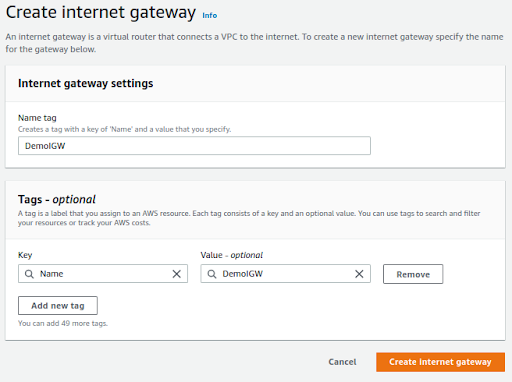
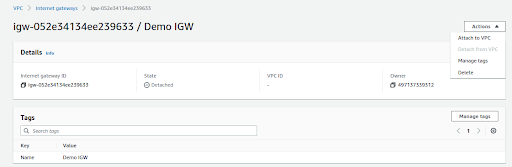
Created IGW will be in detached mode so we need to attach it to Demo VPC
Select DemoIGW, go to Action and click on Attach to VPC and select Demo VPC
This will provide internet access to Demo VPC
Next we need to create Route table
Go to Route table and click on Create route table
Create 2 route table ( private and public route table)
Select PublicRouteTable click on subnet association and click on edit, add both publicSubnets. Same thing we have to do for private subnets.
Go to PublicRouteTable and click on Routes go to Edit routes and click on Add route enter 0.0.0.0/0 as destination and target will be Internet Gateway and save it.
Now try to SSH into Ec2 instance and it will work.
All in all, what is AWS VPC used for? Amazon AWS VPC makes it easy to build a virtual network in the AWS cloud services. You don’t need VPNs, hardware, or physical datacenters. It becomes easy to understand your own network space and manage the way in which your network and the Amazon EC2 resources inside your network are exposed to the internet.
If you need any further information about setup AWS VPC, what is AWS VPC used for, or have any query related to the AWS VPC tutorial, get in touch with our AWS cloud services experts today!

Why Do We Debug Code?

Sjinnovation’s Project Management Process


